Every time when we have something precious, it is human nature to preserve it from any external damage or threat. Be it the money, jewelry, or properties we ensure everything is safe and intact by practicing due security measures. As a result, sighting security guards is no big deal, as the world around is full of valuable things that need to be protected. This has been the case of the physical valuable things but what about software.
Yes, software! Isn’t that important and valuable?
As technology grew eminent in the past few decades, data and software have become much more powerful. With the help of data and software, we can perform various tasks that can yield money and have become a prominent source of income for businesses across the world.
With the growing value and importance of data, the vulnerability around it grew as well. Where the offenses and attacks are made to damage data in order to extract money or do collateral damage illegally.
Since the technological advancements have made a wider reach, even the possibility of such online offenses has increased, with the rise of more data thefts, threats, intrusions, and hacking. This has given birth to the emerging cybercrime that has to be curbed strongly.
It is thus important to ensure a strict practice of security, leading to the rise of Cybersecurity, the branch of technology that deals with the online security of data and software. There are various compliances and frameworks that need to be adopted, in order to ensure the complete safety of the data and software.
Before we discuss the various Cybersecurity Frameworks and decide which one to use when, in order to ensure complete protection, let us first begin with the basics and understand what a cybersecurity framework is and its significance.
What is the Cybersecurity Framework?
Cybersecurity Framework is voluntary guidance, based on the standards, guidelines, and best practices for the various organizations in order to efficiently manage and mitigate cybersecurity-related risks.
It has a prioritized, flexible, and cost-effective approach helps that promotes the protection and resilience of critical infrastructure and other sectors that hold importance for the economy and national security.
The Cybersecurity Framework is a combined effort of the business and government that comprises of the measures, rules, and practices that showcase the security to be the imperative foundation.
It helps the business proprietors and administrators of the critical foundations to oversee the cybersecurity-related hazards and manage them through an organized, adaptable, repeatable and effective approach depicted by these frameworks.
Significance of Cybersecurity Framework
Cyber threats not only leads to the loss of the data but also leads to hefty monetary losses for the companies that strive on the data for their operations. These monetary losses are potentially on a higher side marking Millions and Billions of dollars that could be lost by a company in a single cyber attack.
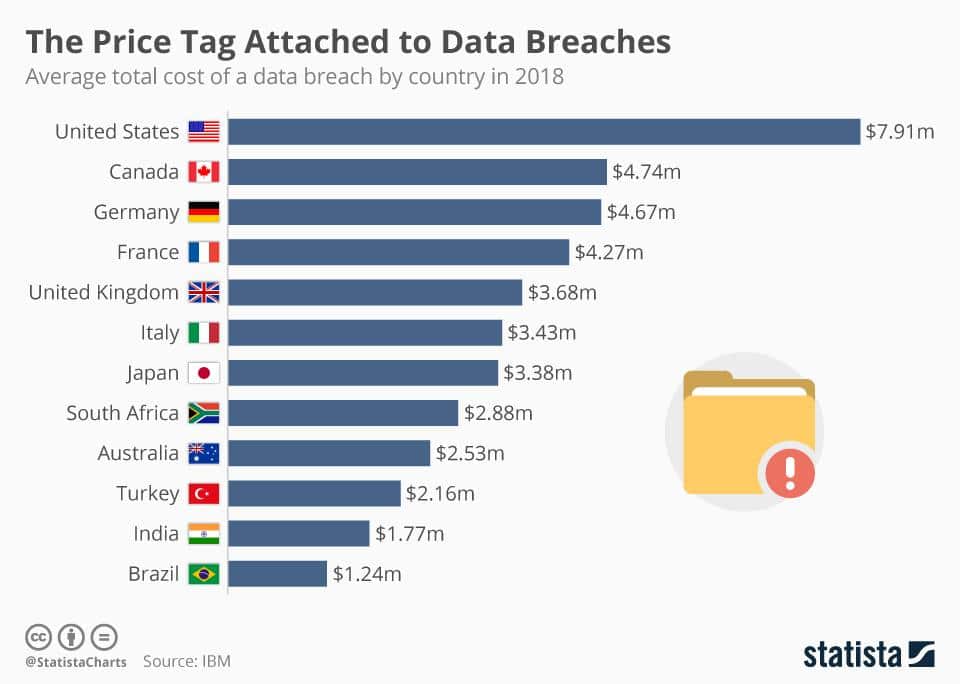
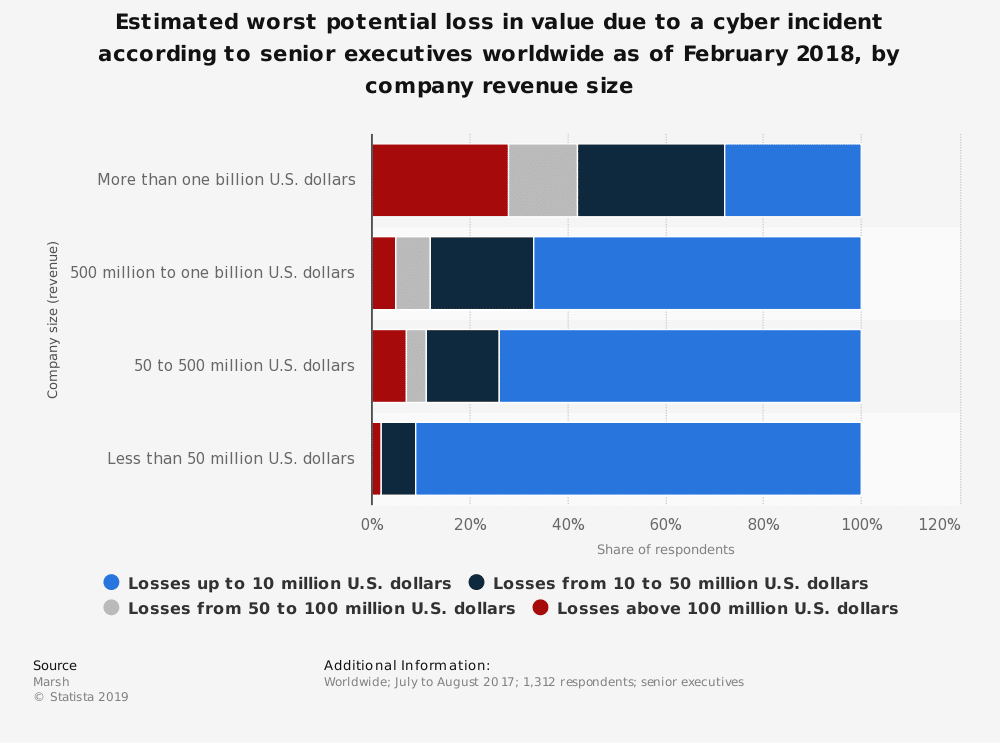
Here’s a study report by Statista, which shows how millions of dollars are lost each year due to data breaches in different countries.
On the other hand, the scale of the potential loss depends upon the size of the company and can even go up to billions for the multi-billion companies, as per the 2018 study report from Statista.
With such huge figures depicting the potential losses, it is clearly indicative and alarming that one needs to follow the proper Cybersecurity measures in order to curb these potential threats and save millions of dollars that are lost each year due to these breaches around the world.
This clearly indicates the need for a strong and diligent Cybersecurity framework that could help the organizations adopt and practice the key measures towards safety from the potential cyber threats.
Types of Cybersecurity Framework
In order to work on different aspects of the cybersecurity of a system, different types of cybersecurity frameworks have been designed to deal with each of them. There are three types of Cybersecurity Frameworks namely:
- Control Frameworks
- Program Frameworks
- Risk Frameworks
What is a Control Framework?
Control Framework is a set of control protocols that protects the data within the IT infrastructure of a system. It acts as a comprehensive security protocol that intends to protect the system against frauds or thefts from the outside parties, that includes hackers, intruders, and other cybercriminals.
Where is the Control Framework used?
The control framework is used for an array of measures that target to ensure the overall security of the system against the potential frauds and threats that are committed by external parties.
This includes identifying the baseline set of controls for the system that distinguishes internal parties from the external ones. It is meant to analyze and assign the controls that should be given based on the roles that each of the stakeholders performs in the system.
To assign the controls, a control framework is used to assess the state of technical capabilities that each of these parties holds, so as to give them the due controls without compromising with the security of the system.
Once the controls are assigned, the framework also takes care of how they are implemented by prioritizing them over one another as they tend to overlap for seamless and secure functioning.
It also involves the development of the initial roadmap for the security team, which they need to follow in the due course of time based on their responsibilities and capabilities as the stakeholders.
NIST SP 800-53 Control Framework
NIST Special Publication 800-53 Control Framework, authored by Joint Task Force, is one of the Control Cybersecurity frameworks that provides guidelines and best practices to protect the government’s sensitive information and citizen’s personal information from the potential cyber attacks. The security controls have three impact baselines namely:
- Low-Impact
- Moderate-Impact
- High-Impact
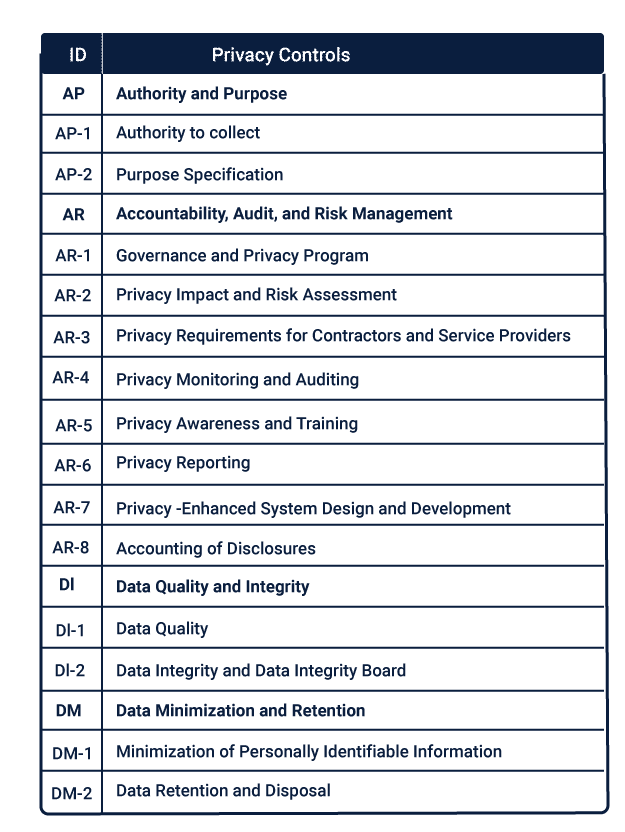
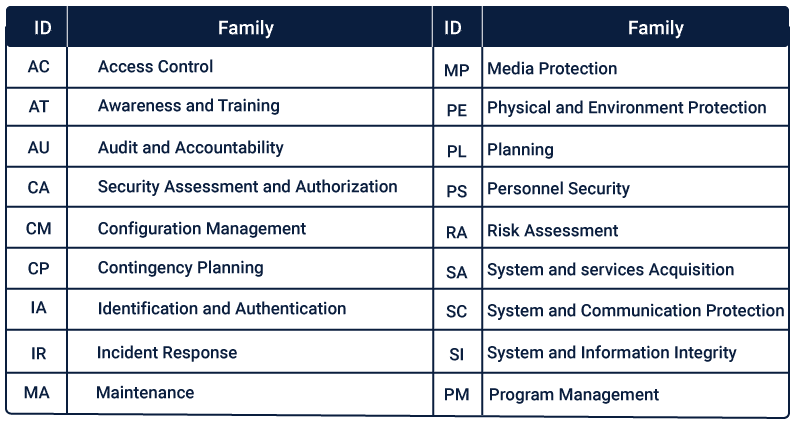
While the Security Control Identifiers for NIST SP 800-53, is broken down into the following Control Identifiers and their respective Family Names.
The Trust model is used to determine the trustworthiness of systems and components based on their ability to meet security requirements, security capabilities, and security functionality along with security assurance based on evidence.
The comprehensive control catalog of security and privacy controls for NIST SP 800-53 is based on Family, Control, and Control Enhancement.
These controls can be implemented based on the priority or security control baselines. When it is based on priority, control is exercised based on the P1, P2, P3, and P0 priority levels.
CIS Control Framework
CIS Control Framework is a cybersecurity framework that intends to identify, develop, validate, promote, and sustain best practice solutions to implement cyber defense. It is a publication of best practice guidelines for cybersecurity.
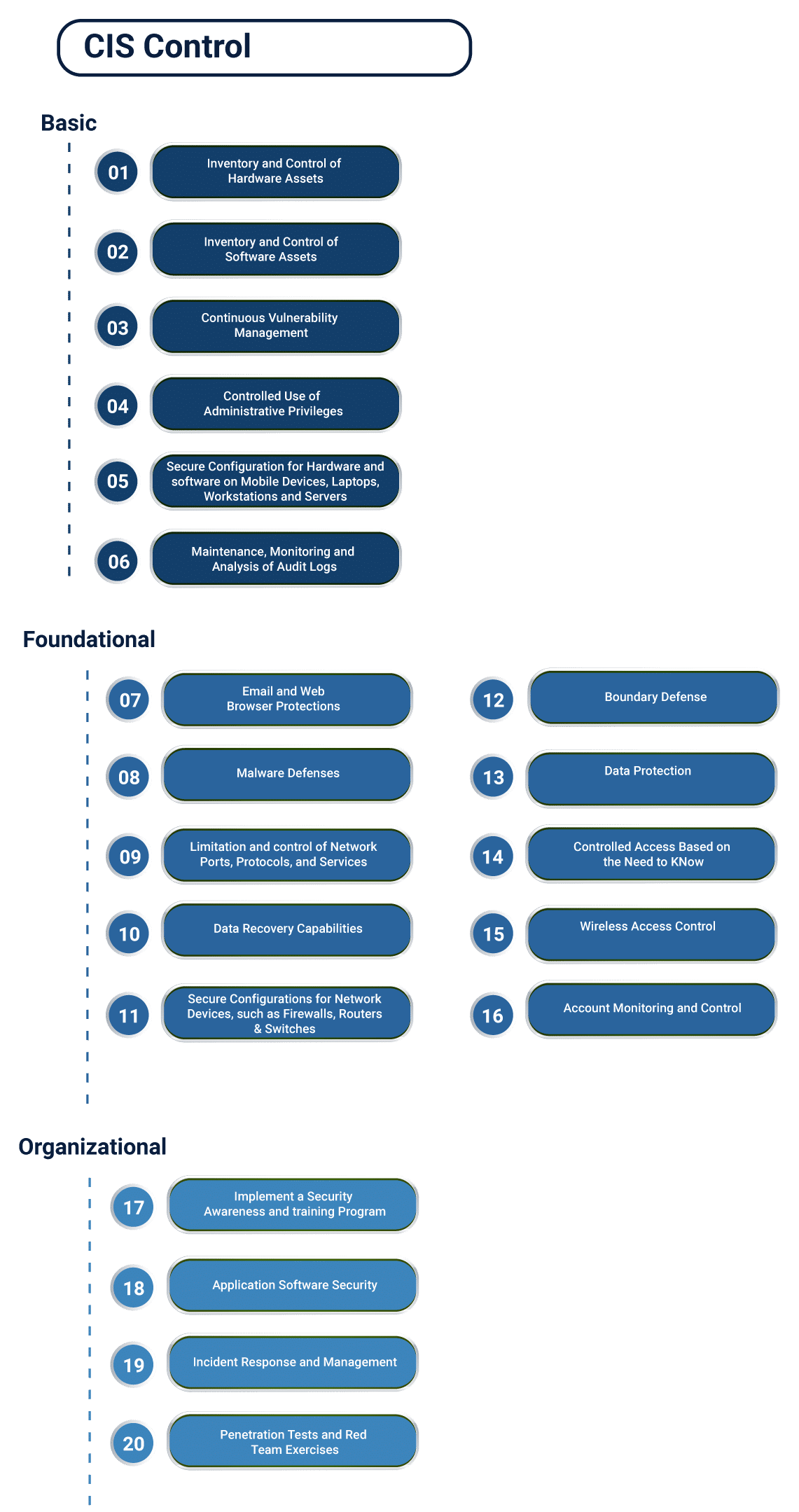
CIS Control Framework consists of 20 key actions, which are termed as CSC (Critical Security Controls). These controls are meant to be followed by organizations who are looking forward to mitigating or blocking known cyber attacks.
The listed controls are classified at Basic, Foundational, and Organizational, where the first 6 controls are basic, next 10 are foundational and the last 4 of them are organizational controls.
Their main goals are to leverage the cyber offense, informing cyber defense, with an intention to focus the high payoff areas. CIS ensures that security investments remain focused on countering highest threats. They aim to maximize the use of automation, so as to enforce security controls, in order to eliminate human errors.
They target to collect ideas that could improve the cyber defense by using the consensus process.
What is a Program Framework?
Program Framework is a set of security and privacy protocols that protect the sensitive data within the IT infrastructure of a system. The framework acts as a comprehensive security protocol that intends to protect the system against frauds or thefts from the outside parties, that includes hackers, intruders, and other cybercriminals.
Where is Program Framework used?
The program framework is used for an array of measures that target to ensure the overall security of the system against potential vulnerabilities.
This includes an assessment of the overall security program to ensure its effectiveness. It is also used in building a comprehensive security program. The program framework is also used to measure the maturity and conduct industry comparisons to ensure that the standards are effectively maintained.
It also aims to simplify the communications within the organization that is conducted with the business leaders.
Overview of the ISO 27000 Series
ISO 27000 series, also known as the family of ISMS Family of Standards or ISO27K series, is a set of information security standards that are jointly published by the ISO and IEC.
These provide the framework of the best practices which are recommended to ensure information security management.
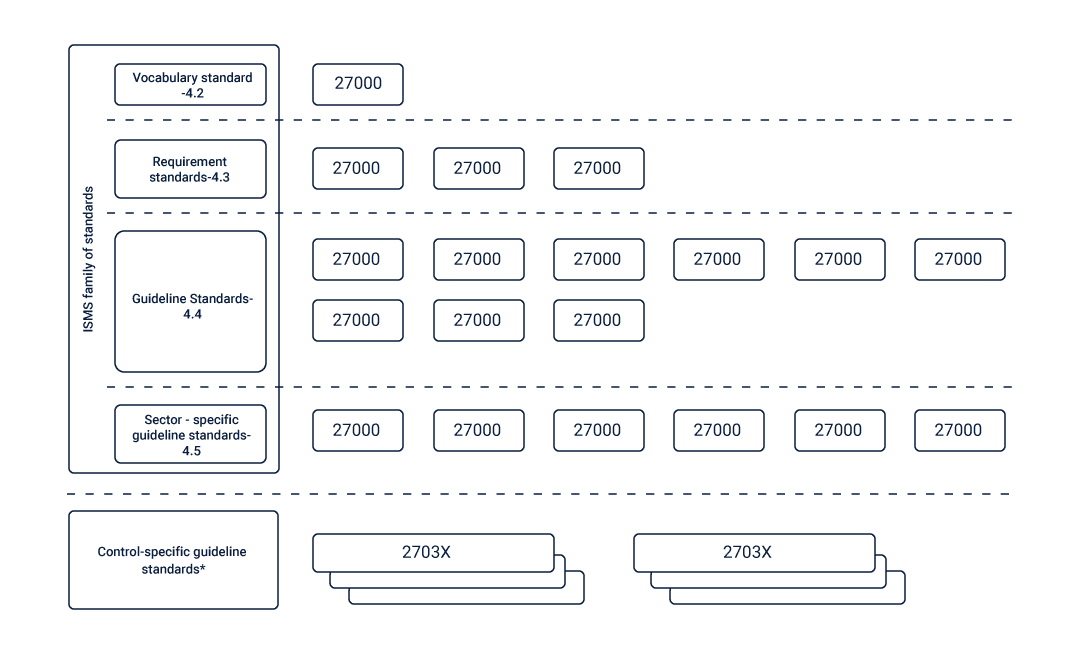
ISO 27001
ISO 27001 is an information security management standard that belongs to the ISO 27000 series. It is a framework that defines the policies and procedures that includes all the legal, physical and technical controls involved in an organization’s information risk management processes.
It does not mandate any specific information security controls, rather it provides a checklist of controls which should be considered in the code of practice. ISO 27001 defines the areas of focus such as organizational context, leadership, planning, support, documentation, operation, performance evaluation and improvement that are important for building a security program.
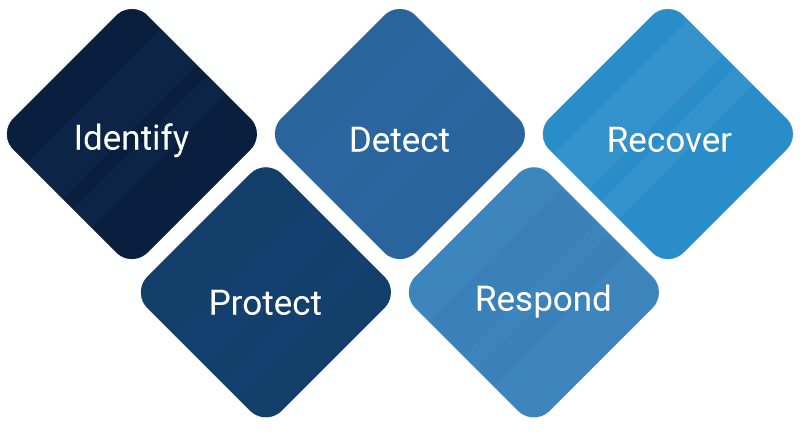
NIST Cybersecurity Framework (CSF)
NIST CSF provides a policy framework of cybersecurity guidance that aims at assessing and improving the ability of organizations to prevent, detect, and respond to cyber attacks, so as to ensure complete cybersecurity.
This framework comprises of three parts namely:
- Core
- Profile, and
- Tiers
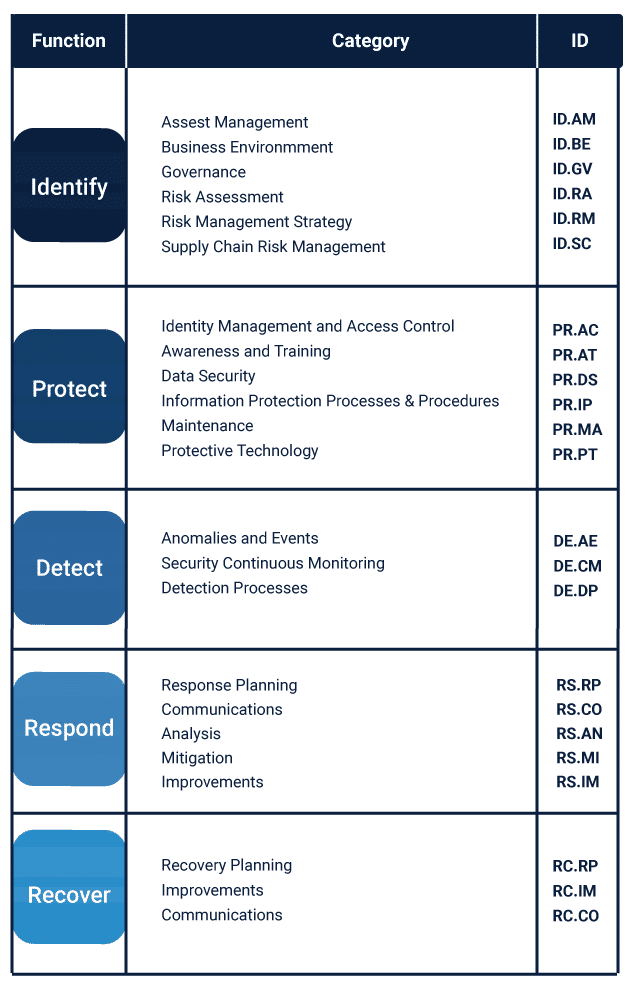
NIST CSF to CIS control Mapping
Various CIS controls can be mapped to the respective NIST CSF functions as mentioned in the image below.
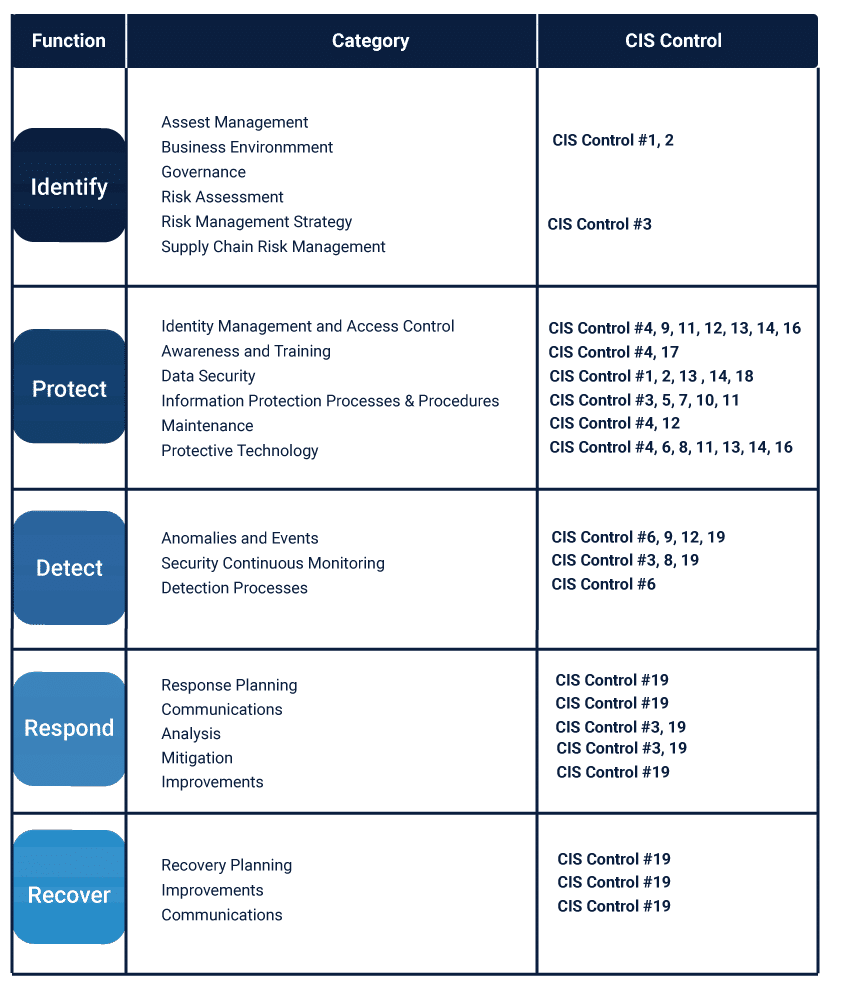
The different cybersecurity frameworks are not mutually exclusive and these can be mapped together to make the cybersecurity of the system more impactful. A mapping between the different frameworks ensures a cohesive approach towards the mitigation of risks and vulnerabilities for the system.
What is a Risk Framework?
Risk Framework is a set of control protocols that protects the data within the IT infrastructure of a system, against any potential risks. It acts as a comprehensive security protocol that intends to assess and manage the potential risks, which may harm the system in different capacities.
Where is Risk Framework used?
A Risk Framework is used for assessment and management of the potential risks that appear for the software. This includes an array of areas that contribute to the overall risk assessment and management.
Risk Framework is used where it is expected to draft and define the key process steps that shall be used for the assessment and management of the risks. It is also used to structure the entire risk program so that the task intended are streamlined end to end.
Risk Framework is used in areas where risk has to be identified, measured or quantified in order to manage it efficiently. It is also used in prioritizing the security activities to ensure that the system is vulnerable due to potential risks.
Overview of NIST Security Risk Standards
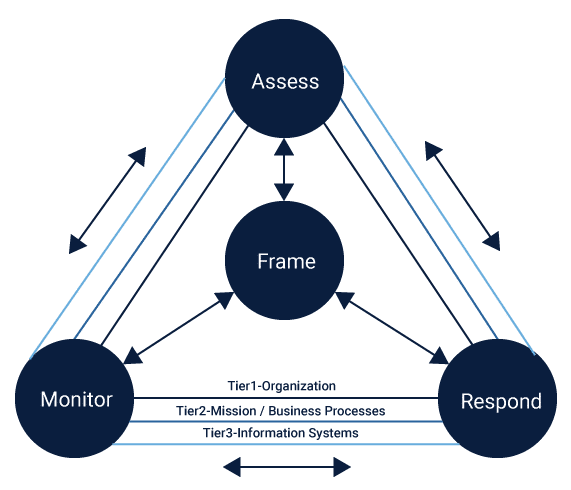
NIST Security Risk Standards consists of framework policies that aim at Assessment and Management of the potential risks. The risk management process is a four-sided process that comprises of steps Assess, Frame, Respond and Monitor respectively.
These are interconnected with each other and work together in coordination to ensure effective risk management. Several NIST Frameworks together ensure that these aspects are completely covered. These frameworks namely NIST SP 800-39 and NIST 800-37 are meant for the risk management process, while NIST SP 800-30 is meant for the risk assessment.
The NIST SP 800-39 targets the overall risk management process, on the other hand, NIST SP 800-37 aims at Risk Management Framework (RMF) for the federal information systems.
While NIST SP 800-30 defines the Risk Assessment process.
NIST Risk Assessment Process
Risk assessment is a process that identifies, estimates and prioritizes information security risks. It happens to be a key component of a holistic, organization-wide risk management process.
Risk Assessment aims at addressing the following points:
- Preparing for risk assessment
- Conducting risk assessment
- Communicating risk assessment results to designated organizational personnel
- Maintaining risk assessments over time.
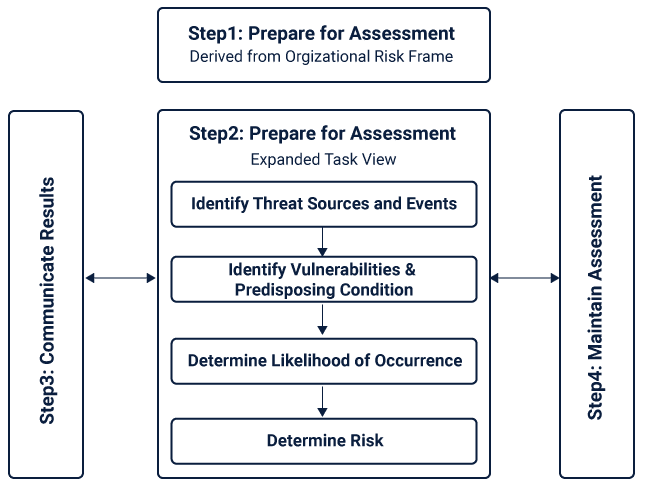
Unlike being a one-time activity, risk assessment is involved throughout the SDLC, across all the tiers in the risk management hierarchy. They aim to highlight the potential adverse impacts to various organizational operations and assets, individuals that are related to the organization, other organizations that collaborate; and the economic and national security interests of the United States.
It requires careful analysis of the threat and vulnerability information so as to determine the extent to which the aforementioned circumstances or events could adversely impact the organization and the probability of its occurrence.
- Preparation for the Risk Assessment
This includes the following tasks which are to be conducted before you begin to conduct a risk assessment for your system:
- Identify the purpose for which the assessment is conducted
- Identify the scope in which the assessment prevails
- Identify the assumptions and the constraints that are relevant to the assessment
- Identify the sources of information that are intended to be used as inputs during the assessment
- Identify the risk model and the analytic approaches that are to be used during the assessment
This includes the following tasks which are to be conducted while you conduct a risk assessment for your system:
- Identify the threat sources for the respective organizations
- Identify the threat events which could be produced by these identified threat sources
- Identify the vulnerabilities that are within the organizations, which could be exploited to cause potential threat events by the threat sources and the predisposing conditions leading to the exploitation.
- Determine the likelihood of the threat events and the probability of them being successful.
- Determine the adverse impacts these threats could pose to the organization and other relevant areas.
- Determine the information security risks which form as a combination of the threat exploitation, their impact, and other uncertainties.
- Communicating the Risk Assessment results
This includes the following tasks which are to be conducted after you conduct a risk assessment for your system:
- Communicate the risk assessment results.
- Share the due information which is developed during the risk assessment to contribute to the other activities meant for risk management.
- Maintaining the Risk Assessment
This includes the following tasks which are to be conducted in order to maintain a continuous risk assessment for your system:
- Monitor the risk factors that are being identified in the risk assessments continuously and understand the subsequent changes, if any occur to those factors.
- Update the risk assessment components as per the monitoring activities of the organization.
With these steps, one can successfully conduct Risk Assessment for the organization in a continuous manner in order to highlight the potential risks which are to be mitigated to ensure the information security of the system.
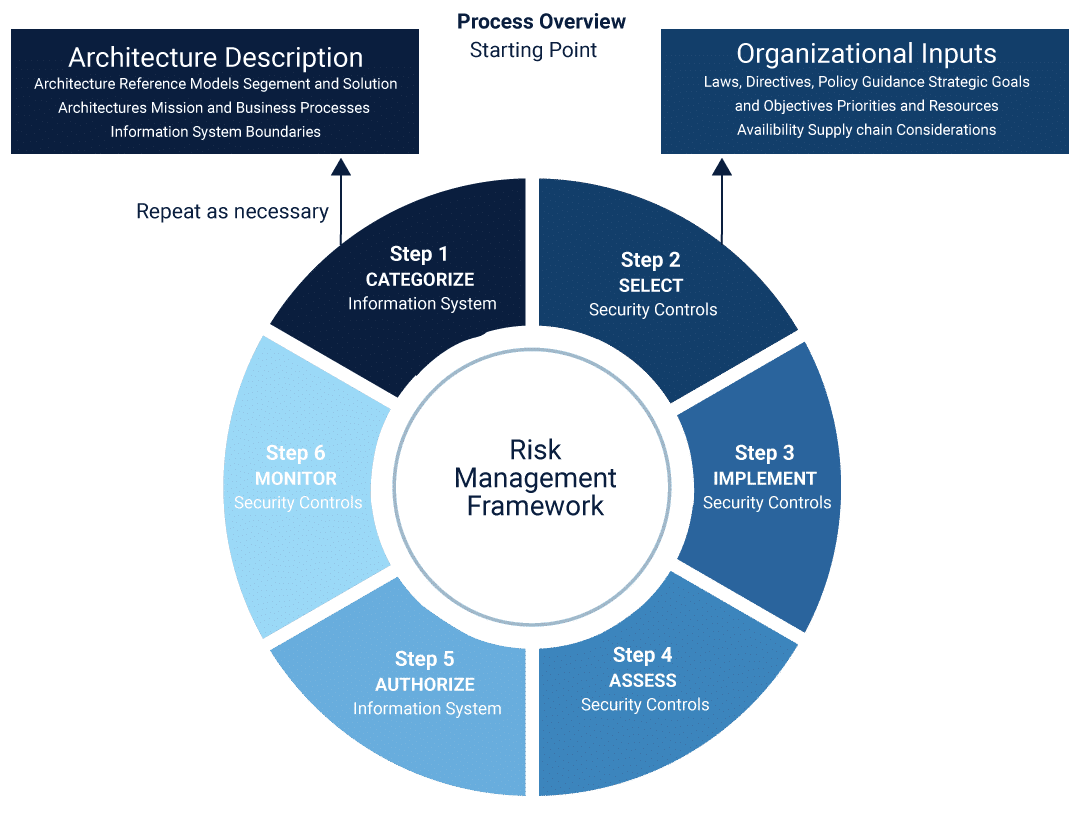
NIST Risk Management Framework (RMF)
NIST Risk Management Framework (RMF) is developed to improve information security, strengthen risk management processes and encourage reciprocity among the organizations. It emphasizes on the management of organizational risk that is the risk to the organization or to the individuals that are associated with the system’s operations.
RMF targets risk management by promoting the development of security and privacy capabilities into information systems at every stage of the SDLC (Software Development Life Cycle). This is done by maintaining awareness of security and privacy, with continuous monitoring of the processes, followed by reporting of noteworthy incidents.
It provides a dynamic and flexible approach to effectively manage security and privacy-related risks in diverse environments, where the threats remain complex and sophisticated, thereby reducing overall vulnerabilities.
NIST Risk Management Framework is a multi-step process that includes:
- Categorize Information System
- Select Security Controls
- Implement Security Controls
- Assess Security Controls
- Authorize Information System
- Monitor Security Controls
NIST SP 800-39
NIST SP 800-39 is a risk management framework that aims to provide guidance for an integrated, organization-wide program for managing information security risk to organizational operations, assets, related individuals, collaborating organizations and national security.
It is a structured, yet flexible approach that targets to manage risk. NIST SP 800-39 is intentionally broad-based, which has specific details of assessing, responding to, and monitoring risk on an ongoing basis that are provided by other supporting frameworks.
These supporting frameworks are NIST SP 800-53, NIST SP 800-30, NIST SP 800-37, ISO 27001 and ISO 27005.
The risk management process that operates across the three tiers i.e. organization, mission/business processes, and information systems, consists of 4 steps namely:
- Frame
- Assess
- Respond, and
- Monitor
NIST SP 800-37
NIST SP 800-37 is a risk management framework which operates throughout the system life cycle to ensure security and privacy. It provides a disciplined, structured, and flexible process for managing security and privacy risk.
NIST SP 800-37 risk management framework includes:
- information security categorization
- control selection, implementation, and assessment
- system and common control authorizations
- continuous monitoring
It promotes responsibility and accountability for the controls that are implemented within an organization’s information systems and inherited by them, by using a multi-step process that includes:
- Categorizing Systems
- Selection of Controls
- Implementation of Controls
- Assessment of Controls
- Authorization of System, and
- Monitoring of the Controls
NIST SP 800-30
NIST SP 800-30 is a Risk Assessment Framework that is modeled to conduct a regular assessment using designated Risk Models. These can be conducted at all three tiers in the risk management hierarchy:
- organization level,
- mission/business process level, and
- information system level.
The risk assessment activities which include Preparation, Conduction, Communication, and Maintenance can be well integrated with the steps of Risk Management Framework (RMF), which are defined in NIST Special Publication 800-37.
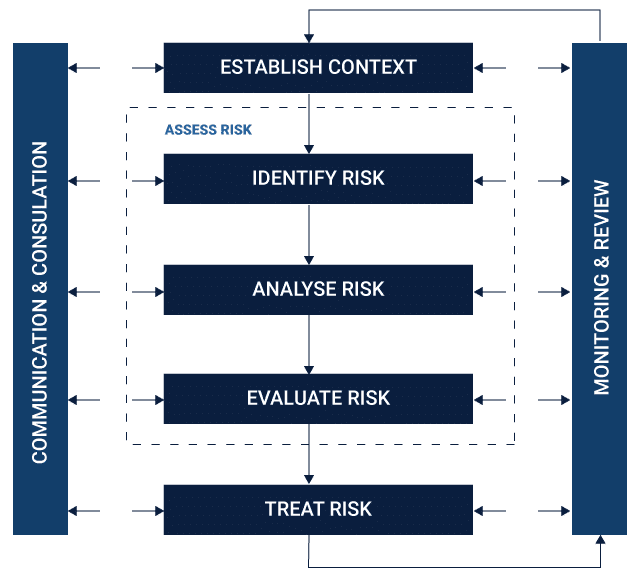
ISO 27005
ISO 27005 is an Information Security Risk Assessment Framework that complies with the international standards, which meets the requirements of ISO 27001.
It does not specify any specific risk management methodology, yet it implies a continuous information risk management process which is based on the following 6 components:
- Context Establishment
- Risk Assessment
- Risk Treatment
- Risk Acceptance
- Risk Communication and Consultation
- Risk Monitoring and Review
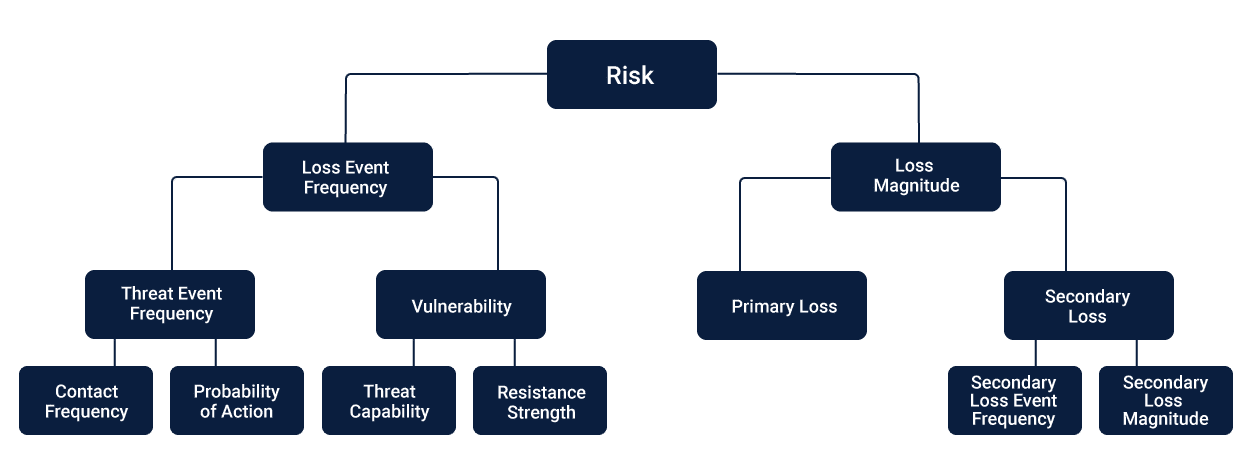
Factor Analysis of Information Risk (FAIR) Model
FAIR (Factor Analysis of Information Risk) is a model that is based on the factors that contribute to risk and how each of them affects each other. It is a risk management framework that complies with the international standards, that aims to help organizations understand, analyze and measure the information risk.
FAIR is a standard Value at Risk (VaR) framework that targets cybersecurity and operational risk. It provides the standards and best practices that enable organizations to measure, manage and report on information risk from the business perspective to the stakeholders such as information risk, cybersecurity, and business executives.
Defining Risk
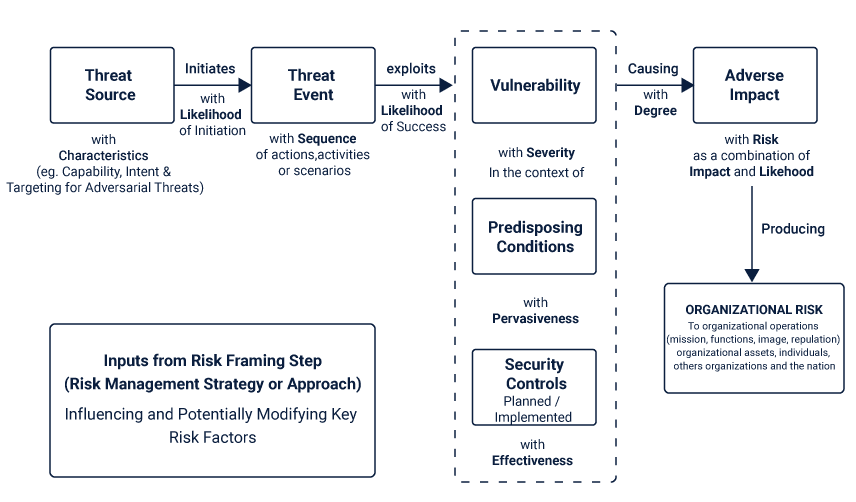
Risk is a measure of the extent to which an entity is threatened by a potential circumstance or event. It is a function of the adverse impacts which occurs, when the given circumstance or event occurs and the likelihood of its occurrence.
Information security risks are those which occur from the loss of confidentiality, integrity or availability of sensitive information. It reflects the potential adverse impacts on the organizational operations, which includes the mission, functions, image, and reputation of the organization. Additionally, it also causes ill-effects on the organizational assets, individuals, other organizations and even to the extent of national security.
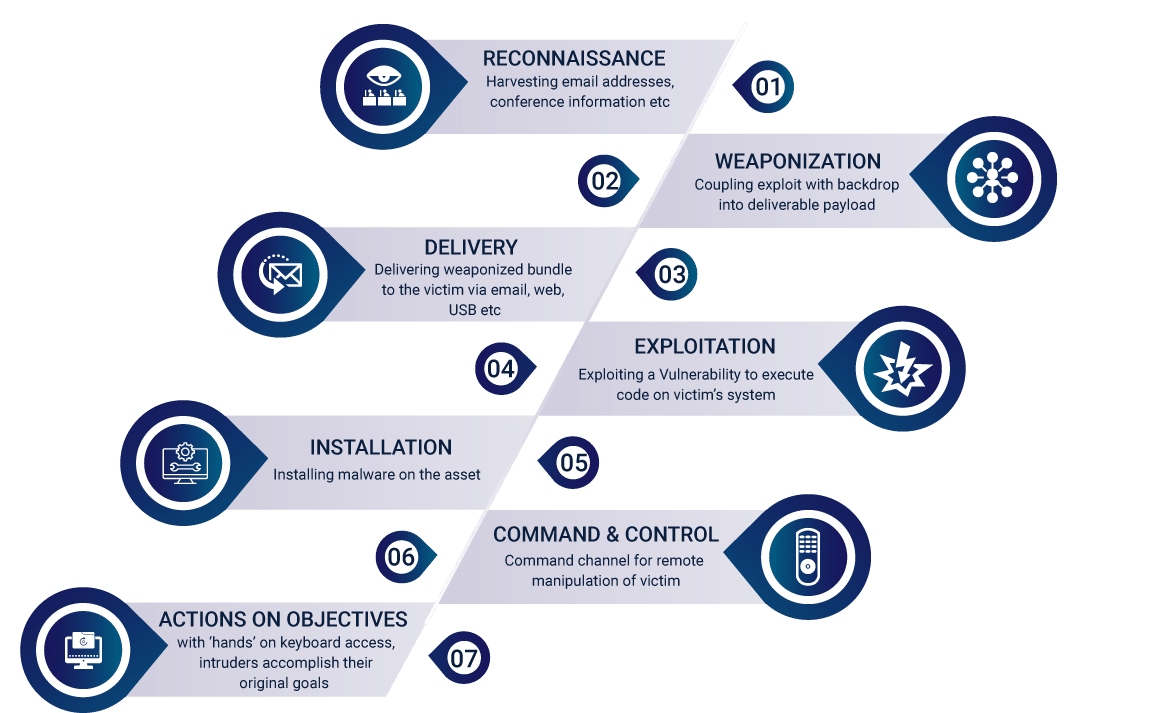
The Intrusion Kill Chain
Intrusion Kill Chain is a systematic approach which targets and engages the adversary in order to make the system secure and reliable eliminating the risks that are being identified. It is an integrated end to end process which is often defined as chain since it is a sequential process, where one deficiency could interrupt the whole process.
Here are the phases of the intrusion kill chain with respect to the Computer Network Attack or Computer Network Espionage:
- Reconnaissance
This phase includes the research, identification, and selection of targets. These targets are often represented as crawling Internet websites such as conference proceedings and mailing lists for email addresses, social relationships, or information on specific technologies.
- Weaponization
This step includes the coupling of a remote access trojan with an exploit, into a deliverable payload, by using an automated tool, which is also known as a weaponizer. Often, client application data files such as Adobe Portable Document Format (PDF) or Microsoft Office documents serve as the weaponized deliverable for this phase.
- Delivery
This phase includes the transmission of the weapon to the targeted environment. The three most prevalent delivery vectors for the weaponized payloads by APT(Advanced Persistent Threat) actors are email attachments, websites, and USB removable media.
- Exploitation
After the weapon is delivered to the victim host, the next phase is where the exploitation triggers intruders’ code. Exploitation tends to targets an application or operating system vulnerability, but it could also exploit the users themselves or leverage an operating system feature that auto-executes the code.
- Installation
This phase of the intrusion kill chain marks the installation of a remote access trojan or backdoor on the victim system, that allows the adversary to maintain persistence inside the environment.
- Command and Control (C2)
In this step, the compromised hosts establish a C2 channel by beaconing outbound to an Internet controller server. APT malware requires manual interaction instead of conducting the activity automatically. Once the C2 channel establishes, intruders have “hands on the keyboard” access inside the target environment, which they can leverage.
- Actions on Objectives
Once they have the “hands on the keyboard” access, intruders can take actions that help them achieve their original objectives of data exfiltration which involves
- collecting, encrypting and extracting information from the victim environment;
- violations of data integrity or
- availability are potential objectives as well.
Alternatively, the intruders could wish to access the initial victim box for use as a hop point so that they can compromise additional systems and make a lateral move inside the network.
The intrusion kill chain is a model for actionable intelligence, where the defenders of the system tend to align the enterprise defensive capabilities to relevant processes which an adversary undertakes to target that enterprise. Defenders measure their performance and the effectiveness of these actions, to plan investment roadmaps and rectify capability gaps if any.
Applying Cybersecurity Frameworks to achieve the most of it
These risk assessment and management frameworks, that have been discussed above target the areas of systems, which are vulnerable and tend to get exploited by the intruders. By applying these measures in a cohesive and coordinated manner, you make the best out of them.
These cybersecurity frameworks that are designed as per the international standards, ensure the best of the cybersecurity when practiced duly in a regular manner by making the system secured in a multi-dimensional way, averting all the possible risks by eliminating vulnerabilities with a strong check.
It is only possible to leverage these frameworks to the behest of the system’s security when they are inclusive in the regular operations, where the entire team is well aware of them and practice them at every step of the software development life cycle.